The Hybrid Cipher Is More Popular These Days Because
Google DoubleClick IDE cookies are used to store information about how the user uses the website to present them with relevant ads and according to the user profile. Like most technologies encryption has evolved throughout the years from simple origins.
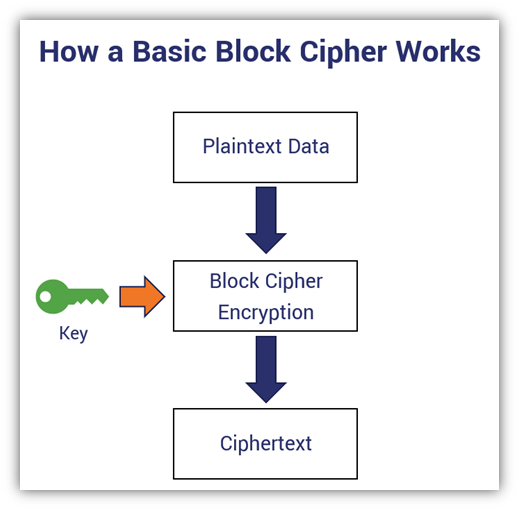
Block Cipher Vs Stream Cipher What They Are How They Work Hashed Out By The Ssl Store
Stream Cipher and RC4 Stream Cipher is a Symmetric key cipher where the plain text and the pseudo-random key key stream are combined by xor operation.
. Answer 1 of 7. The hybrid cipher is more popular these days because a. We have offices in 26 countries in all 5 continents.
Encrpyt b cipher text bits into the next block to generate b more keystream bits IV makes it non deterministic use. The light was good and so from that moment on light was separated from darkness. The private key is made of two numbers apart from 1 and the number itself.
Web development programming languages Software testing others. The public key is a large number everyone can get. There are only 25 rotations to try by brute force.
The Vigenère cipher works by applying a Caesar cipher to each letter but the amount each letter is shifted by depends on a key The Vigenère cipher is more secure than the Caesar cipher because its harder to spot the patterns in the ciphertext that can be used to help break it The most commonly used letter in the plaintext will always be the. Hence it is sometimes called a session. 5 months 27 days.
An alternate name is the cipher state where the encryption of. It works by using a public-key cipher to share a key for the symmetric cipher. For example if the G cipher is used then A becomes G B becomes H C becomes I and so on through the alphabet.
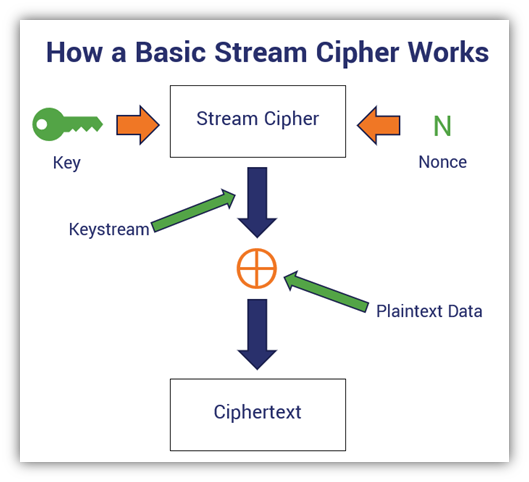
ROT1 is just one of these ciphers. This is one of the most widely used types of codes or cipher. Encrypt b plaintext bits XOR with keystream to generate b ciphertext bits 3.
It is a very weak technique of hiding text. Electronic Code bookECB Cipher Block ChainingCBC Cipher FeedbackCFB Output FeedbackOFB and Counter Mode CTR Describe Electronic Code Book ECB related to symmetric block ciphers. First block - encrypt IV - generate b keystream bits 2.
It uses public key cryptography for encryption for key material exchange and symmetric key for more efficiency. Illustrate a hybrid system using Diffie-Hellman as the public key system and DES as the symmetric cipher. Let there be light.
1What ciphers are available to use and how do you decide which is best for you. The classical algorithms are those invented pre-computer up until around the 1950s. ChaCha20 has just turned 10 and is now becoming popular but was essentially unheard of 10 years ago.
A hybrid cipher uses both a symmetric cipher and a public-key cipher. If spaces are preserved in the encoding its easy to see where the word breaks. While modern encryption relies on complex computational operations older encryption ciphers were rudimentary and easy to break.
In Caesar cipher the set of plain text characters is replaced by any other character symbols or numbers. A person only needs to be told which Caesar cipher was used to decipher a message. In Caesars cipher each alphabet in the message is replaced by three places down.
For any block of plaintext the cipher is always the same eg. 1 year 24 days. There are two levels of ciphers classical and modern.
It uses public key cryptography for encryption to have a long-key based encryption and symmetric key. The following output displays. Globalism means that every action you.
-instead of using block to encrypt to generate the next cipher it uses cipher text Process. It uses public key cryptography for encryption to have a long-key based encryption and symmetric key for key exchange for more efficiency. Since symmetric key sharing is secure the symmetric key used is different for each message sent.
Security is the most challenging aspects in the internet and network applications. The earth was formless and empty darkness was over the surface. Cipher is part of Prosegur.
The cipher command displays the following output. 10 reason why you should choose Cipher. Internet and networks applications are growing very fast so the importance and the value of the exchanged data over the internet or other media types.
The actual message being sent is then encrypted using the key and sent to the recipient. Encrypting files in CUsersMainUserDocuments Private OK 1 file s or directorie s within 1 directorie s were encrypted. Transposition Cipher was the most often used conventional cipher in the early days because it was resistant to frequency analysis.
For securing the key more the DES algorithm 7 is used to encrypt the key which generates the cipher 1 which the encrypted key for decryption process. Historical Cryptography Ciphers. We are part of a huge publicly-traded group.
The light was called day and the darkness was called night. A hybrid cryptosystem uses both public key and symmetric key cryptography to obtain the benefits of each. The hybrid cipher is more popular these days because a.
The hybrid cipher is more popular these days because It uses public key cryptography for encryption to have a long-key based encryption and symmetric key for key exchange for more efficiency. Follow this answer to receive notifications. To enable encryption on the Private directory used in the previous example type.
Peace of mind can come from knowing that your cybersecurity partner has the resources to make anything happen. Regardless of each ciphers strength all encryption methods share a common goal to encode. In the encryption each byte of plain text is encrypted with the corresponding character of the key stream.
Closely related to Caesar Ciphers are Substitution Ciphers. Illustrate a hybrid system using RSA as the public key system and AES as the symmetric cipher. If the Y cipher is used then A becomes Y B becomes Z C becomes A and so on.
The purpose of this study is to provide another way of encrypting information through transposition and substitution cipher with salting which is a common method to hashing. It is modern and is made of two keys the private and the public key. By far RC4 is the most popular stream cipher thats been around for 10 years.
The start of Cipher. None of these algorithms are very secure as far as protecting todays computer data goes so if data security is needed then modern algorithms should be used. These two numbers are multiplied together and can produce.
The aim behind this cipher is to keep all the original. These still map 11 between each character in the source text and cipher text but adjacent characters in the source do not have to map to adjacent ones in the destination. Abc will always equal fct.
The start of Cipher - Cipher.
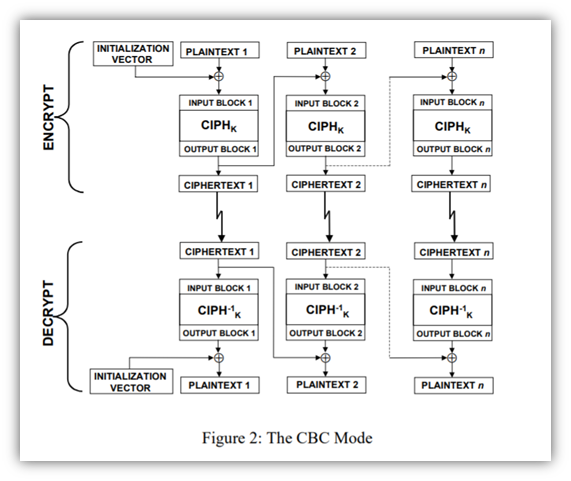
Block Cipher Vs Stream Cipher What They Are How They Work Hashed Out By The Ssl Store
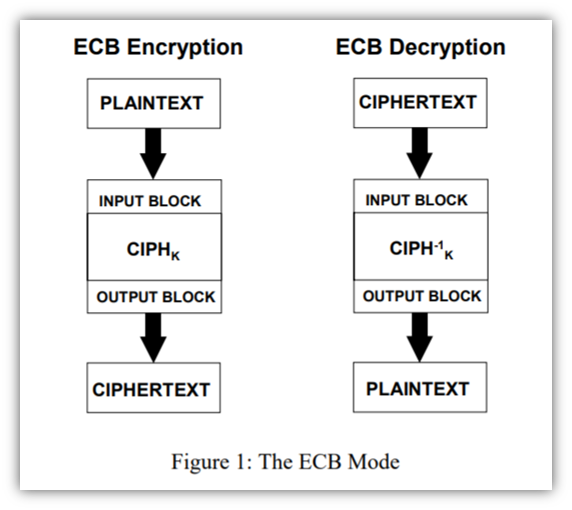
Block Cipher Vs Stream Cipher What They Are How They Work Hashed Out By The Ssl Store
Block Cipher Vs Stream Cipher What They Are How They Work Hashed Out By The Ssl Store
0 Response to "The Hybrid Cipher Is More Popular These Days Because"
Post a Comment